Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
What is a BEC Attack? (And How to Prevent Them)
What is a BEC Attack? (And How to Prevent Them)
As emails zip back and forth across the internet, sneaky cyber threats are constantly lurking in the shadows. One of these threats is called Business Email Compromise, or BEC for short.
BEC attacks trick companies into sending money or sharing private info without even realizing they’re being scammed.
In this guide, we’ll dive deep into the world of BEC scams. We will uncover what they are, the different types, and how to stand guard against these digital tricksters.
What is BEC?
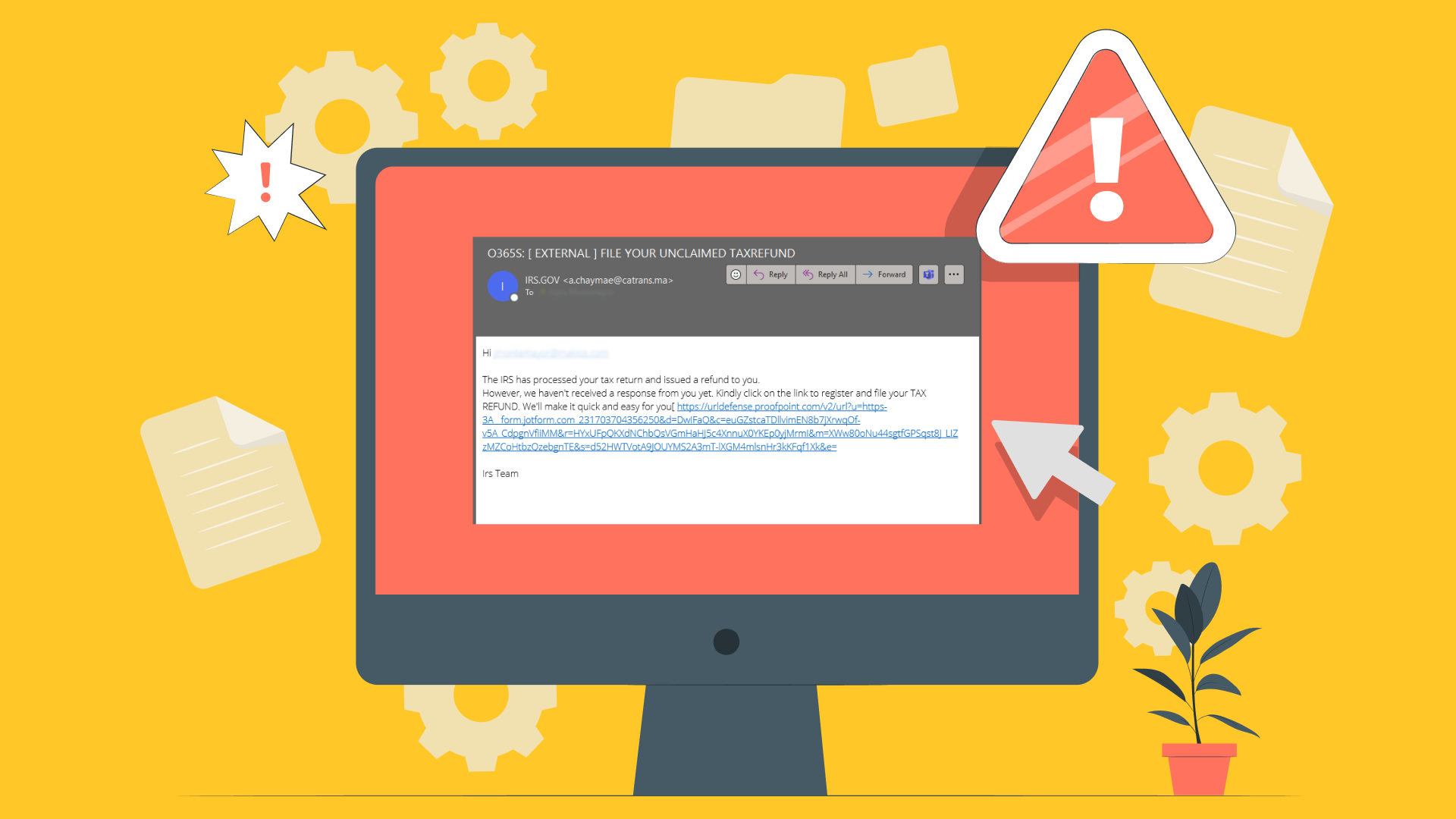
Business Email Compromise (BEC) is a type of cyber scam that targets companies using email fraud. It’s not your typical spam email about winning a lottery.
BEC attacks are clever and cunning. They’re designed to trick even the smartest and most cautious employees.
Scammers pretend to be someone you trust. They could act like your boss, a co-worker, or a business partner, asking you to wire money or send sensitive information.
The goal? To steal money or valuable data from businesses. Often, these scammers leave people scratching their heads wondering how they fell for it.
Types of Business Email Compromise You Should Know About
BEC attacks come in different types, each with its own twist. Here are a few you should keep an eye out for:
- CEO Fraud: Imagine getting an email from your CEO saying they need a large sum of money wired somewhere urgently. That’s CEO fraud. It’s a fake but it looks real enough to trick you into acting fast, without thinking twice.
- Bogus Invoice Scheme: This one’s like receiving a bill from a company you know and work with. Except the bill is fake. It is sent by scammers hoping you’ll just pay it without checking its authenticity.
- Account Compromise: In this scenario, someone’s work email gets hijacked. Then, it’s used to request payments or sensitive info from others within the company.
- Data Theft: When it comes to data theft BEC scams, attackers aren’t after cash. They want confidential info, targeting departments like HR or finance. They try to grab personal or financial data about the employees or the business.
Knowing these types of BEC scams can help businesses stay alert and protect themselves from falling victim to these increasingly common and costly attacks.
Who is at Risk of BEC Attacks?
Think of BEC attacks like a net cast wide into the ocean that aims to catch any fish, big or small. No business is too large or too small to fall victim to BEC attacks.
From giant corporations that span the globe to the small mom-and-pop shop at the corner of your street. Everyone is a target.
Industries that deal with lots of suppliers or regularly perform wire transfers tend to be the main targets of these cyber sharks. This could include industries like manufacturing, finance, and healthcare.
But in reality, any company that uses email can find itself in the jaws of BEC. It’s all about staying vigilant.
BEC attackers are always looking for their next victim.
How Do BEC Attacks Work?
BEC attacks are well-planned and often follow the same general steps. Here’s how these scammers try to get you:
Step 1: Research
The attacker picks their target and starts gathering information. They might look at company websites, social media, or any public records to learn about the company’s dealings.
They’ll also find details about its employees and even the way they communicate.
Step 2: Impersonation
Armed with information, the scammer takes on a new identity.
They might pretend to be the CEO, a trusted vendor, or even a co-worker. This is where the scam begins to take shape.
Step 3: Crafting the Email
With a fake identity ready, the attacker crafts an email. This isn’t just any email—it’s designed to mimic the tone, style, and even the signature of the person they’re impersonating, making it look as real as possible.
Step 4: The Request
This is the heart of the BEC attack. The email will usually ask for something urgent such as a wire transfer, sensitive information, or access to confidential systems.
It’s all made to seem very pressing, playing on the victim’s sense of duty or fear of disappointing a superior.
Step 5: The Steal
If the victim falls for the scam and follows through on the request, the attacker makes their move. Money is transferred, information is handed over, or access is given.
Just like that, the scam is complete.
Each step of a BEC attack is carefully thought out to exploit trust, authority, and the routine nature of business communications.
Recognizing these steps can help individuals and companies spot BEC attempts before they become successful attacks.
Why Are BEC Attacks Dangerous?
BEC attacks are like silent alarms. They don’t come with a loud bang or a clear warning sign, making them extremely dangerous.
Here’s why:
- Financial Losses: The most immediate threat of a BEC attack is the financial hit a company can take. Imagine sending thousands, or even millions, of dollars to a scammer, thinking you’re paying a vendor. That money is often impossible to get back.
- Damage to Reputation: Trust is hard to earn and easy to lose. If word gets out that a company fell for a BEC scam, customers and partners might question how safe their information and money are with that company.
- Legal and Compliance Issues: Depending on the information lost or the nature of the financial transactions, companies might find themselves in hot water with regulators, facing fines or sanctions.
- Emotional and Morale Impact: Falling victim to a BEC attack can be a demoralizing experience for the team involved. It can create an atmosphere of mistrust and paranoia.
BEC attacks target the very foundation of business operations. Negatively impacting trust in communication.
This makes them particularly dangerous and damaging on multiple levels.
How Do I Improve BEC Detection?
Detecting BEC attacks is all about looking for clues and questioning things that seem out of place. Here’s how you can sharpen your detective skills:
- Educate Your Team: Knowledge is power. Teach your team about BEC scams. Let them know what to look out for like urgent financial requests or emails asking for sensitive information.
- Verify Requests: If you get an email asking for money or information, take a moment to verify it. A quick phone call or face-to-face chat with the person who supposedly sent the email can reveal a lot.
- Use Email Filters: Many email systems can be set up to spot potential BEC attempts, flagging emails from outside the company that pretend to be from executives or employees.
- Monitor Email Habits: Keep an eye on the normal email habits of your team. If someone’s sending style suddenly changes, it could be a sign their account has been compromised.
- Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security, making it harder for scammers to access your company’s email accounts. Even if they manage to get a password.
Improving BEC detection is about staying alert, questioning things that don’t seem right, and using the right tools to stop these scams before they can do damage.
It’s a team effort that requires everyone to play their part.
Protect Against BEC Attacks with Makios Technology
In the fight against BEC attacks, Makios Technology offers powerful tools and services designed to shield your business from these email threats.
Here’s how Makios Technology can help:
- Advanced Email Security: Makios provides top-notch email security features that catch and filter out suspicious emails. It’s like having a highly trained guard dog that barks whenever a stranger comes too close to your digital doorstep.
- Employee Training Programs: Knowledge is your best defense. Makios offers training programs to teach your team how to recognize and respond to BEC attempts. It’s like giving everyone in your company their own detective badge.
- Regular Security Audits: With Makios, you can have regular check-ups on your company’s email security health.
Partnering with Makios Technology means you’re not facing the threat of BEC attacks alone. You have a team of experts armed with the latest tools and knowledge to keep your business safe.
Fortify Your Business Against BEC Scams
BEC attacks are a serious threat. But with the right preparation and partners like Makios Technology, you can protect your business from these digital dangers. Be proactive, stay alert, and work together to keep the gates locked tight against cyber threats.
If you want to make sure you’re protecting your company from BEC scams,
get in touch with Makios Technology today!
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.